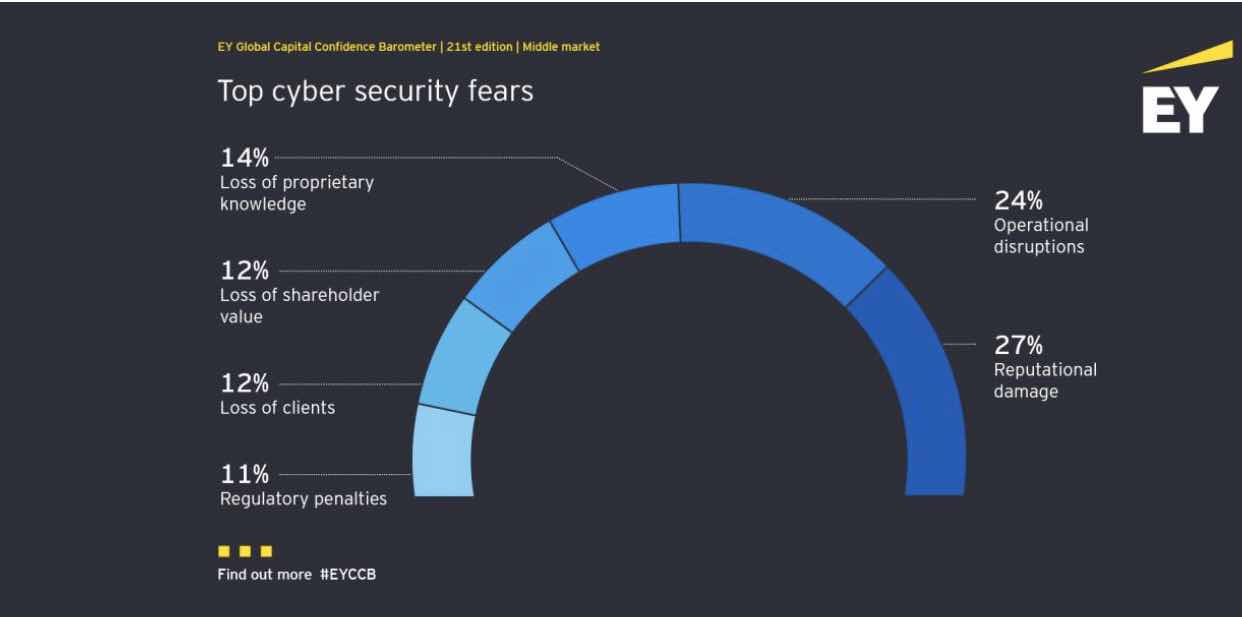
Mid-market companies may not think they are a target for cyber crime, but they are actually at the top of the list.
According to the October 2019 EYGlobal Capital Confidence Barometer, The 2 biggest fear that middle-market companies the have about cybersecurity is
- reputational damage.
- Second on the list is operational disruption.
This is no surprise, given the harm that cyber attacks have caused to many large brands around the world.
Those mid sized firms with between US$50m and US$3b in revenue — should be concerned about the reputational damage an attack can cause.
The EY Global Capital Confidence Barometer asked mid-market firms about their biggest barrier to using data as a competitive advantage: 27% said exposure to cyber threats is the biggest barrier, second only to increasing regulation at 28%.
Lack of confidence in their security means they are afraid to monetize the data they have captured through channels such as customer profiling and targeted advertising.
They are also right to be worried about operational disruption, given the size of the potential financial impacts. And mid-market firms should be much more concerned than they are about all the different impacts of cyber attacks, as they are more vulnerable compared to larger organizations and typically have insufficient defenses.
Cybercrime can cause a midsize firm to go out of business
The highly sophisticated, ever-changing nature of cyber crime makes it nearly impossible for mid-market companies with scant resources to keep abreast of the threats.
Many attackers aim to use mid-market firms as Trojan horses for attacks on larger companies. Targeting massive companies is relatively more difficult, because these organizations usually have dedicated cybersecurity teams and systems, so an easier way to attack them is through their suppliers.
For example, an attacker might try to plant malicious code in the supplier’s application, which will then find its way into the larger company via their business relationship.
Although a breach of this nature would generate more negative publicity for the larger company, the mid-size company would likely suffer reputational and financial damage, as the companies it supplies may cancel contracts and blacklist it. It might not be as public, but it will be financially painful. In a worst-case scenario, this disruption could cause the mid-size firm to go out of business.
Another problem is that insufficient cyber defenses are leading some companies to lose competitive advantage.
Large vulnerability
Every mid-size company we talk to knows that cybersecurity is an issue. But the size of the threat, and the time and resources needed to defend it, are major challenges for them.
Many don’t have the funds or human capital to deal with the constantly shifting technologies involved.
This is exacerbated by an industry-wide deficit of cybersecurity talent, which leads mid-market companies to have a less informed understanding about what security and controls they need. Talent in cybersecurity is much rarer compared to systems implementation, development and maintenance.
Consequently, there are not enough people with the right skills to provide companies with customized advice at affordable prices, or even respond to issues. There is also insufficient data available to help mid-size firms establish the right levels of control.
A mid-market company should integrate cybersecurity requirements across the organization as they design their business and as they continue to innovate.
Kris Lovejoy EY Global Advisory Cybersecurity Leader
Regional issues
Some regional variations surfaced in the EY Global Capital Confidence Barometer. For example, mid-market companies in China were more concerned about the threat of regulatory penalties linked to cybersecurity than those in other countries.
This isn’t surprising, given the strict China Internet Security Law that went into effect in 2017.
Another regional issue we see is that most of the available cybersecurity budget and talent is in the US. In other markets — including South and Central America, the Middle East, Africa and Asia‑Pacific — these resources are much more limited. Considering that most of the world’s population lives in these areas, this creates a huge mismatch.
Also, many mid-market companies in the US and Europe use outsourced technology or support based in emerging markets, where there is limited cybersecurity talent or capability. In fact, much of the affordable technological innovation in the market now comes from such countries.
It is therefore relatively easy for attackers to bury or hide themselves in such small emerging-market companies and wait for a mid-market company to acquire their services. In this way, the mid-market firm can suddenly find that they themselves have been the victim of a Trojan horse attack.
Again, the mid-market companies we work with have seen this happening and know it is an issue. But they generally do not know how to respond, and they do not have a security plan fit for their businesses. In most cases, the robust cyber plan is developed and implemented after a breach.
The smaller companies that mid-market firms buy from are even less likely to have good cybersecurity. As a result, mid-market firms must be sure to check before buying any software or services, as well as before making any acquisitions of smaller companies.
Mid-size firms are often innovative, which tends to mean they rely on contract resources but do not always check the quality of the code they are integrating. Also, some assume that, when buying network connectivity, IT services and cloud applications, cybersecurity comes installed. But that is not necessarily the case. Such vendors can provide those services, but mid-size firms must check in advance before there is any integration of systems or data. In fact, they must not assume that any of their partners — whether core technology suppliers or not — has the right level of security.
Because of these vulnerabilities, we cannot emphasize enough how large a target mid-market companies present to attackers. If your company provides services to bigger companies — for example, updating hardware in smart meters — you may not think you are a prime target of cyber crime. In fact, you are at the top of the list. You must think about it less from a size or industry perspective and instead ask: “What risk do I pose to others?”
If your company provides services to bigger companies, you may not think you are a prime target of cyber crime. In fact, you are at the top of the list.
Ryan P. Burke EY Global Growth Markets Leader
Security by design
It’s clear that mid-market companies need to invest more in this area, given the size of current and potential threats. But it is not just about size of spend — there is not necessarily a correlation between investment level and security success. The organizations that are best prepared have made security part of everything they do. In other words, they don’t think in terms of a dedicated budget; rather, they design security inside every new product, procurement and business service from the beginning as a competitive differentiator. This makes their security much more efficient and means they will spend less over time.
They need the right advice to do this. Mid-market companies often lack the resources that larger companies have for cybersecurity. We therefore do not advise that they major in cybersecurity, but instead build relationships with partners who can show them what good cybersecurity looks like and help them implement controls and assess them regularly. In most instances, you can outsource or co-source many of these services today.
Don’t be afraid
Our most important advice on cybersecurity is to not ignore these issues or let them overwhelm you. Do not be afraid to learn and ask questions.
That’s much better than waiting for someone to tell you what to do because you have been breached or because additional regulation has been forced upon you. Invest in software development and application security testing.
Conduct additional penetration testing on your systems to identify your security gaps. Outsource (or co-source) core security services to trusted providers with the skill and capacity to protect your business.
Our experience with middle-market companies is that they are often reactive rather than proactive — they do not get serious about cybersecurity until after they have been attacked.
But if they address these issues sooner, it will cost them far less in the long run.
